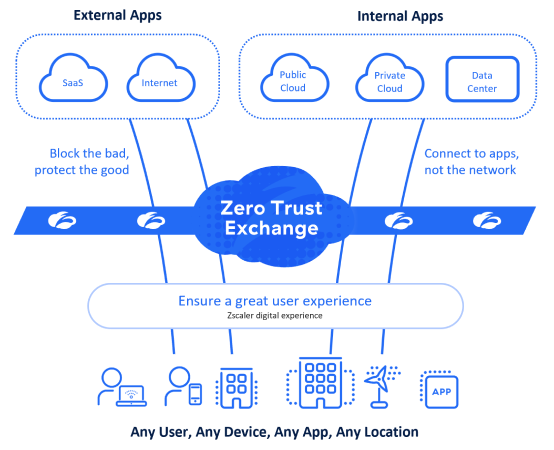
- Over 550 patents issued and pending
- Multi-tenant architecture
- Distributed across 160+ edge locations
- Direct peering with the largest Internet destinations
Explore our infographic
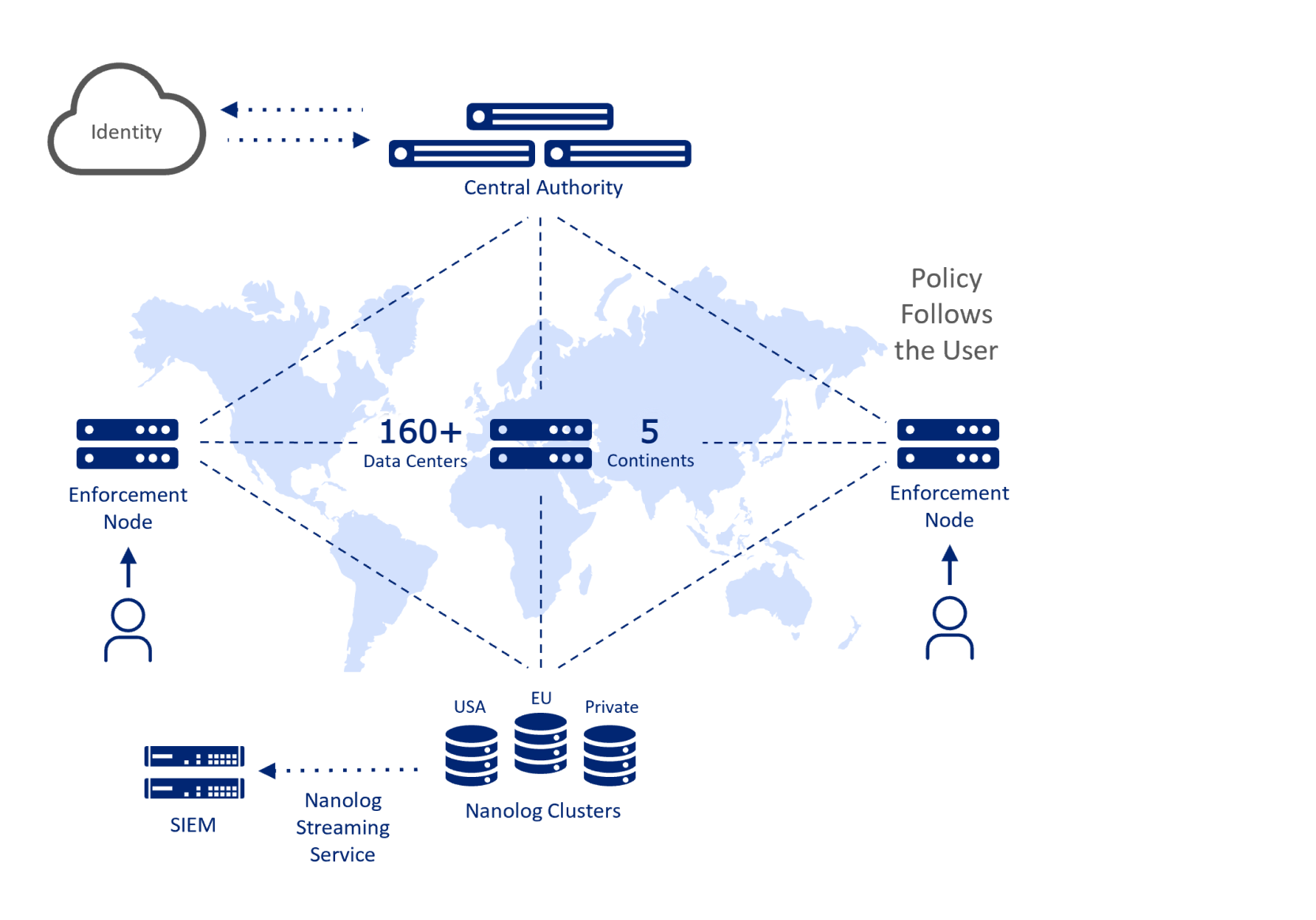
Control plane
Zscaler Central Authority (CA) monitors our entire security cloud and provides a central location for software and database updates, policy and configuration settings and threat intelligence. The collection of CA instances together act like the brain of the cloud, and they are geographically distributed for redundancy and performance.
Data plane
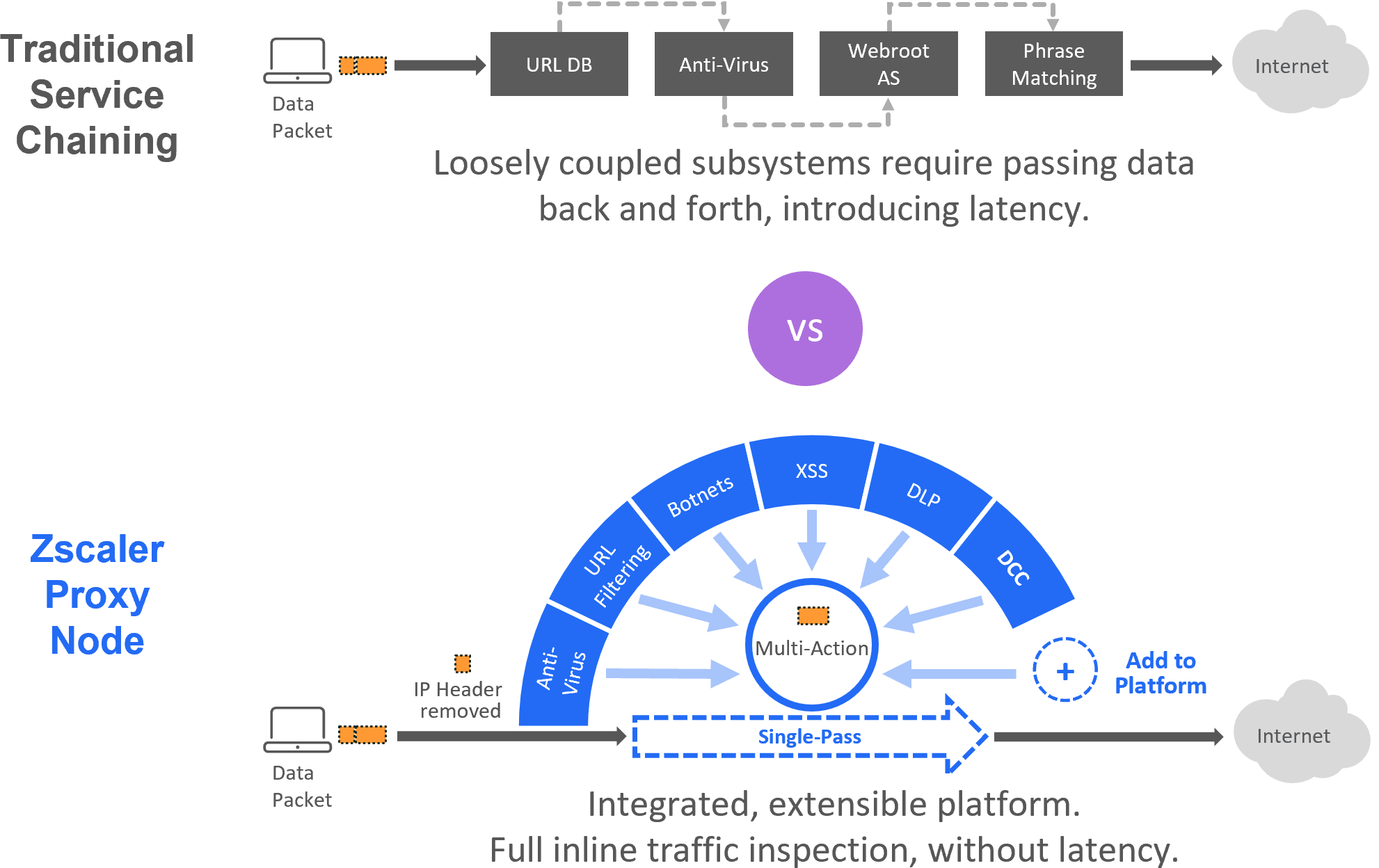
Customer traffic gets directed to the nearest Zscaler Enforcement Node (ZEN), where security, management and compliance policies are enforced. Our differentiated authentication and policy distribution mechanism that enables any user to connect to any ZEN at any time to ensure full policy enforcement. ZEN utilizes a full proxy architecture for in-line traffic inspection and is built to ensure data is not written to disk to maintain the highest level of data security. Logs are continuously created in memory and forwarded to our logging module.
Log Plane
Compressed logs are transmitted to our Nanolog Servers over secure connections and multicast to multiple servers for redundancy. Our dashboards provide visibility into our customer’s traffic to enable troubleshooting, policy changes and other administrative actions. Our analytics capabilities allow customers to interactively mine billions of transaction logs to generate reports that provide insight on network utilization and traffic. Regardless of where users are located, customers can choose to have logs stored in the US, the EU or Switzerland as well as streamed to a third-party SIEM.